How to Protect a Campus With Proper Perimeter Security
An expert reviews perimeter security best practices based on NFPA 730’s deter, detect, delay tactic.

Editor’s Note: This story first ran in Security Sales and Integration’s sister publication Campus Safety.
It is an unfortunate fact that today’s world is filled with an excessive level of violence levied against our society; particularly our campuses and businesses. As we look at the various means of minimizing the damage caused by these acts, it’s important to go through a thought process related to available products that can be combined to minimize these events.
We also must not only look at what has happened but also what can happen. Additionally, we should be aware of other less violent but equally important potential problems.
If we take a minute to look at NFPA 730, a guide for premises security, we can find guidance from the Concentric Circles of Protection: deter, detect, delay and respond. From this, we can build a comprehensive and layered protection program.
The first layer involves the perimeter. In evaluating a campus, it’s critical to begin with a vulnerability assessment, which should begin at the perimeter.
That being said, a perimeter can be difficult to define. Does it encompass the campus itself, just a building or multiple buildings? Are there multiple perimeters? Since the design of sites is so varied, it is up to the individuals who are responsible to make the determination as to what will work best for their site.
In all cases, begin by including the outer reaches of your perimeter. That should include parking lots, athletic fields and any outlying buildings relative to school, university or healthcare facility activities.
Cameras, ALPR, Fences, Gate controls & Emergency Call Systems Help Detect Trouble
Looking at the outer limits or the full property, we will begin with products, technologies and other solutions that can alert the proper authorities at the earliest stages. This then is the “detect” ring in our Concentric Circles. Such detection products include but are not limited to security fences, gate control, emergency call systems, security cameras and advanced license plate recognition (ALPR).
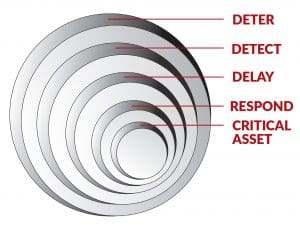
NFPA 730 is a guide for premises security that includes the Concentric Circles of Protection, pictured here.
Perhaps the most significant of those is ALPR. ALPR features optical character reading that converts a vehicle’s license plate to a data stream that will automatically be checked against various databases to immediately report an unwanted visitor.
These unwanted visitors can come from blacklist databases that are available or by entering the information about a specific individual who has been banned from campus.
Realizing that there may be many entrances to campuses, this could be difficult to restrict. However, the potential for early detection is critical in all cases. It is recommended that where possible, a single point of entry should be utilized.
Secure fence systems can include features that will alert you to attempts to cut, climb or pull on the fence where the products are installed.
A proper system should ignore all disturbances by meteorological phenomenon, including vibrations from passing vehicles and should be able to report any instances immediately.
Video systems should include proper lighting and not be restricted to areas that are within range of the structures. Parking lots should be well lit, as should all areas between the parking areas and the structures.
Some athletic fields are out of view of all structures and cameras. A solution might be using solar panels and wireless networking to bring video to those remote areas. Here again, the secure fence systems can be utilized.
Wide Variety of Solutions Can Help Deter & Delay
As we move to the physical buildings, we will focus on the “deter and delay” elements of our circles. Products that will assist in delaying or deterring actions could include bollards and planters, in addition to changes in the campus physical structure.
We want to look at typical means of entry by students, staff, patients and visitors, as well as areas of mass gatherings, such as cafeterias or gymnasiums. We want to assess the means of entry to buildings from the parking areas, keeping in mind that these structures have multiple uses. Lighting for these areas is critical when evening events are occurring.
Restricting access to well-defined areas is critical to protecting students, faculty, staff, patients and visitors. For example, on K-12 campuses, we know that the start and end of school days must allow for easy movement for students; however with proper planning and training, those times can be minimized and protection offered by school personnel.
Doors should only be unlocked for a minimum amount of time, and late entries should only be allowed after the individuals have been screened by video verification or “eyes on” prior to granting access. By creating a proper vestibule for students, patients, staff and visitors entering and exiting the building, we create the opportunity to establish more effective lockdown capabilities and minimize the potential for unwanted visitors.
We have to remember that the threats we face might be from a non-custodial parent or patient family member. Thus, an important component of your system should be a visitor management program. A scan of a driver’s license can produce unexpected results, such as an injunction against a parent, guardian, spouse or other family member or visitor. That scan ideally should be done in the vestibule area with a true man-trap capability so that the interior space is secure.
While we want our campuses to be pleasant environments, we also want them to be secure from a physical attack. There should be no glass, in either windows, doors, sidelights (side windows) or glass corridors from 40 inches to the ground. In lieu of full light (window) doors, or two light (window) doors, door openings should have glass that is no larger than 8 inches by 60 inches.
That is enough to allow light to penetrate, but not enough for a person to shoot out and crawl through. Existing two light or full light doors can be modified or replaced, as can sidelights. Changes could include metal or aluminum panels instead of glass.
The object here is to delay a person from entering a structure. The goal is not to stop firearms from penetrating these panels, but to change the point of attack. If there is an attack from the exterior, changing that point of attack to a level that requires extra effort to gain entry can further delay the intruder. Laminated glass above those areas will eliminate the shattering and easy entry into buildings, further delaying the intruder.
Are all means of entry/egress on the perimeter of your building secure? There are many means of entry and exit in all buildings. In order to secure your perimeter, you should at the least have door position switches or latch bolt monitoring on all exterior openings. This will allow you to be aware of a potential breach of perimeter from the interior of the building (such as a student letting a friend in to vandalize).
Start Asking Questions About Campus Access
As you look at areas of mass gatherings, cafeterias, assembly areas, gymnasiums, auditoriums, can you say that they are safe from attack? Can someone back up a rental truck to a cafeteria to affect an Oklahoma City type tragedy? If so, then you may want to look at bollards to keep traffic a safe distance away. In designing schools, universities and hospitals, terracing or stone walls can be attractive yet prevent vehicles from being parked near these areas of mass gathering.
How protected are your service entries? Can a person gain entry through a loading dock? If so, consider fences or removable bollards.
Can someone drive a truck onto your football field during a game? Here again, terracing or concrete walls with vehicle entries protected by removable bollards can provide a barrier. The walls don’t have to be high, just high enough to prevent vehicle access.
Enterprise Access Control Solutions Help Monitor Systems
As we move forward with these systems it begs the questions, “How do we monitor all of the various systems and whose do we use?” The answer to those questions can be found in an enterprise-class access control system.
That being said, the most effective access systems should feature software that is fully interoperable so as to maximize the various products that are on the market. A fully integrated access product is restricted to the components developed with it. There is no flexibility to change components of that system. A fully interoperable system, however, can often incorporate existing manufacturer’s products into one system. It doesn’t restrict your options to one source.
For example, you may have the option to choose between two or three different video management systems or different visitor management systems. A fully integrated access system does not allow you to do this. You should be able to choose between various systems and software products based on what you have and your needs.
Most importantly, the access control system should feature a federated command and control mapping product that will allow all of the various products, cameras, fence alarms, door position switches, flow valves, smoke detectors, vaping detectors (this issue seems to be growing at alarming rates); to be “mapped” as customizable icons.
Doing so causes an alarm from any point on the map to immediately give an indication and allow the administrator to click on the alarm point, or related cameras etc. in order to make a quick and informed decision as to what the appropriate action should be.
The advantage of the command and control feature is that you can operate and control your system from the icons on the map without having to move to any other software product. This element of the access software is the one control mechanism to allow fully integrated protection for your students, patients, clinicians, faculty and staff.
Good Perimeter Security Can Mitigate Losses
Regrettably, we are not in a position to think that we can stop all acts, but with a prudent look at each facility, we can reduce our losses and potentially deter people from committing unthinkable acts.
In this article, we have not advanced beyond deter, detect, delay. The next element of protection lies in the “Respond” ring. As we move to that next ring, we can examine our current means of notification truly is outdated.
Bob Stosse is a technical sales representative from Keri Systems.
If you enjoyed this article and want to receive more valuable industry content like this, click here to sign up for our FREE digital newsletters!

Security Is Our Business, Too
For professionals who recommend, buy and install all types of electronic security equipment, a free subscription to Commercial Integrator + Security Sales & Integration is like having a consultant on call. You’ll find an ideal balance of technology and business coverage, with installation tips and techniques for products and updates on how to add to your bottom line.
A FREE subscription to the top resource for security and integration industry will prove to be invaluable.







