Meeting New Cyber Protocols to Play in Public Sector
It’s become imperative for integrators to be dialed in on cybersecurity standards and practices. Learn about new guidance from NSA and other federal agencies bringing military-grade controls to commercial environments.

(Image: Tierney/stock.adobe.com)
If you or your organization could deploy the same type of systems used by the military to protect against nation-state and domestic cyber threats, would you? If you wanted to implement security products controls that met the same security requirements to protect you against signal jamming, eavesdropping and interception used by nuclear submarines and jetfighters, could you?
If the answer to both questions is yes, then any organization that has high cyber-assurance requirements need look no further. The solution is provided by the Commercial Solutions for Classified, or CSfC (pronounced ciff-cee) strategy.
High assurance computing equipment was once cost prohibitive and realistically only available to specialized high-risk industries such as defense, government, energy, transportation, law enforcement, public safety and the national intelligence communities.
Those were the kinds of organizations able to afford the capital equipment, as well as the operational and management cost to manage and support these types of systems. We’ve seen firsthand accounts of intellectual property theft, ransomware and fines being imposed on corporations for failing to meet minimum security requirements.
Real-world nation-state exploitation and cyberwarfare against the United States and its allies from Russia, China, North Korea and Iran increase our need for collaboration and coordination between government, public, private, and academic institutions. High-risk systems classified as Critical Infrastructure Protection Sectors and Services (CIP) are regulated by U.S. federal law.
These expensive, mission-critical high assurance systems were subsidized through taxes, fees, grants and other economic incentives that were paid to defense contractors supporting the defense industrial base. Due to the lowering cost of technology, systems and solutions are now being vetted and validated by the U.S. Department of Defense (DoD) and the National Security Agency (NSA).
They are available under the CSfC program. In managing CSfC, NSA mitigates myriad physical and cyber challenges where mission assurance for national security and defense applications are tested and verified. For too long, manufacturers have attempted to circumvent security controls due to cost, resource or supply chain concerns.
Testing is performed by independent organizations known as Common Criteria Test Labs (CCTLs). They map specific performance objectives to multitiered, multidefense layered techniques used when adversarial compromise results in the loss of life, loss of assets or substantial consequence to our national security.
Vendors and manufacturers desiring to be included in CSfC applications must submit their product for testing and define which Capabilities Packages (CPs) map to specific objectives and mission assurance requirements by military and classified organizations.
CPs define products and integrations that undergo stringent evaluation and once approved become allowed to process, store and transmit sensitive information within environments to include secret and top secret classified environments.
Why CSfC Is for You
The increasing technical capabilities of sophisticated nation-state and domestic adversaries against the U.S. and the decreasing ability to defend against new and emerging threats are compelling reasons why all committed to the mission of security should take notice.
This includes technologies such as quantum computing, artificial intelligence and automated scripts (bots) that use machine language and scripts to seek out system vulnerabilities and set the stage for attack from malicious actors. Nearly three-fourths (74%) of cryptocurrency payments have been generated through ransomware attacks and globally up to 10% of all ransomware payments are linked to Russia.
Along with NSA and DoD, the Cyber Security and Infrastructure Security Agency (CISA) is among the U.S. federal agencies that frequently publishes new advisories, notifications, and threat intelligence regarding adversarial intentions and capabilities from these actors.
Nearly 30 years ago, DoD directed all agencies to use commercial off the shelf-technologies (COTS) whenever possible. During that time there was a lack of standardization and interoperability with DoD contractors that sold single-source solutions that did not integrate with other mission required systems.
Now that widespread adoption of policies that include “Cloud first,” and shared services have paved the way for mainstream adoption of more secure and interoperable technologies under the National Information Assurance Partnership to validate the conformance of IT products to standards established by the National Institute of Standards and Technology (NIST) and the NSA.
Capability Packages Explained
There are several prevalidated CSfC solutions known as “Capability Packages” (CPs) approved by the NSA that allow integrators and companies to implement their own solution following the guidelines and restrictions to create an architecture with specific commercial products configured in a particular manner.
CSfC CPs use a reference architecture and configuration model that ensures the components selected permit the necessary functionality. These products are tested using a process known as Common Criteria Evaluation and tested against a Protection Profile (or PP) that defines specifically what the system is expected to do and how it accomplishes its objective.
Potential CSfC vendors pay for technical review, and certification by a government-approved Certified Testing Laboratory (CTL) demonstrating the goal of independently validating the achievable, repeatable and testable evaluation of each technology component implemented within a system.
End users benefit by using CSfC solutions that have been well-vetted and that eliminate ambiguity in architectures that are incompatible or do not achieve the mission assurance objectives that the system was intended to perform. Some of the available CPs include:
- Mobile Access
- Campus Wireless LAN
- Multi-Site Connectivity
- Data at Rest
- Wireless Intrusion Detection
- System/Wireless Intrusion Prevention
End users also benefit by using CSfC CPs offering organizations to implement high assurance risk models to reverse the attack surface and enable you to confidently meet stringent regulatory requirements. This also provides a clear understanding of system functionality, and predictable, reliable, operation and functionality within the environment.
To illustrate how CPs work, we will use the Multi-Site Connectivity (MSC) Capabilities package (see diagram below). The MSC package consists of a nested, layered encryption package known as the black, gray, and red network. The NSA has approved this package as a remote tool that can securely connect users from an untrusted network (i.e. the Internet) to other secure networks that are secured at different security classification levels.
The black network can be managed by an untrusted third party, however, the solution owner must be able to block any unwanted protocols. One specific use case outlining the benefit of CSfC is the ability for IT support personnel from within the intelligence community and military to work from alternative or Work From Home (WFH) environments.
Previous requirements to perform classified support required onsite customer visits. Using a WFH environment can result in 40% operational cost efficiency and productivity increases by enabling a remote workforce capable of performing classified operations remotely.
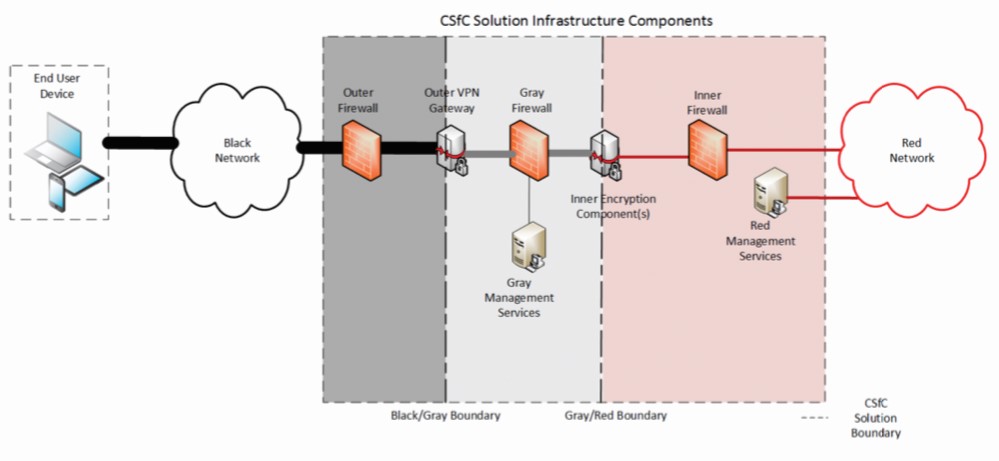
The red/black concept, sometimes called the red-black architecture or red/black engineering, refers to the careful segregation in cryptographic systems of signals that contain sensitive or classified plaintext information (red signals) from those that carry encrypted information, or ciphertext (black signals). (Courtesy of NSA.Gov)
Impact to Integrators
A strong case could be made that every organization in the U.S. (regardless of size, revenue or sector specific market) should consider and evaluate what their security objectives and requirements are to determine if they can shift to adopt a trusted computing model and CSfC-approved CP. This represents a challenge to the security systems industry to modernize IT infrastructures and immediately transition to next-generation systems and services.
This undertaking will include capital, workforce reskilling and a comprehensive review of common interoperability platforms. While the disparity of system types and deployment models is very wide, evolution and adoption of software-defined networking, Cloud computing and emerging technologies that include AI and blockchain leverage stronger mechanisms for audit, access control, protection of data at rest and overall information assurance.
The security integrator’s role will change dramatically. Along with the CSfC program comes a role of the CSfC trusted integrator. Trusted integrators support the client in the implementation of the various CSfC CPs to ensure secure and proper solution functionality.
To become a CSfC trusted integrator, you must complete a questionnaire and be interviewed by the NSA CSfC Program Management Office and demonstrate your proficiency, knowledge and program level understanding to implementation of conformant solutions.
Remaining Vigilant
Shifting to CSfC will be no easy task, especially during the global pandemic, and now emerging military conflicts in the East, resulting in increased cyber-network exploitation activities against the U.S. However, the benefits of deploying far outweigh the cost avoidance and risks.
Declining cost and greater levels of interoperability and security make it imperative to deploy best-of-breed, verified product components and integrated technologies available immediately. Lengthy testing and evaluation within individual organizations is not viable with the current adversarial threats we now face.
Benefits from the deployment of these CSfC solutions include supply chain validation and formal technical approval by government-approved validation labs that use stringent test and performance metrics to determine the suitability of end-to-end integrated products that specifically address the organizational mission need.
Anyone that requires high assurance cybersecurity would be well advised to use CSfC solutions as a baseline to increase their security posture.
Darnell Washington is President and CEO of SecureXperts.
If you enjoyed this article and want to receive more valuable industry content like this, click here to sign up for our FREE digital newsletters!

Security Is Our Business, Too
For professionals who recommend, buy and install all types of electronic security equipment, a free subscription to Commercial Integrator + Security Sales & Integration is like having a consultant on call. You’ll find an ideal balance of technology and business coverage, with installation tips and techniques for products and updates on how to add to your bottom line.
A FREE subscription to the top resource for security and integration industry will prove to be invaluable.







